Solution to the Nitroba case
UPDATE (June 16, 2011): This blog post has been modified in consent with Dr. Simson Garfinkel since the Nitroba case is actively being used in digital forensics classes. The actual solution to the case has now been replaced with hints and clues.
I recently received a request to help solve a network forensics case called "Nitroba University Harassment Scenario".
I regularly keep track of publicly available pcap files on the Internet, but this one was new to me. I therefore dived in and started analyzing the pcap file.
Case Description
The slides describing the Nitroba case present the following scenario:
You are a staff member at the Nitroba University Incident Response Team. Lily Tuckrige is teaching chemistry CHEM109 this summer at NSU. Tuckrige has been receiving harassing email at her personal email address.After locating the NAT:ed private network from where the harassment emails are sent from the scenario continues with:
- Tuckrige's personal email is lilytuckrige@yahoo.com
- She thinks that it is from one of the students in her class.
"To find out what's going on, Nitroba's IT sets up a packet sniffer"Good for us, this means we have some captured packets to analyze with NetworkMiner!
While the traffic was being sniffed Lily received a new email, this time with a link to a webpage with a message titled "you can't find us" and the content "and you can't hide from us. Stop teaching. Start running."
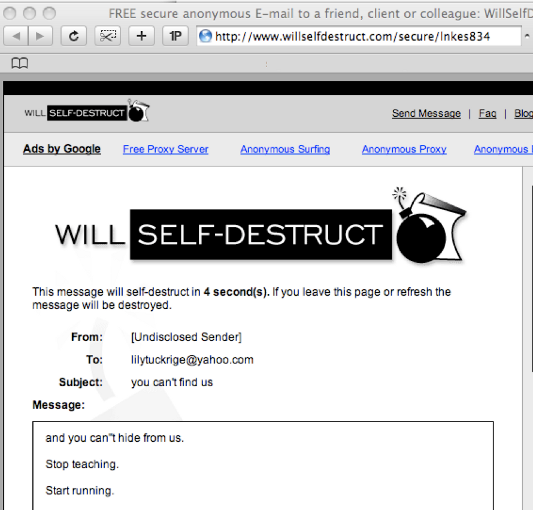
Clues to solving the Nitroba case
Here is a short writeup of hints and clues to how the Nitroba case can be solved:
A good starting point is to look for the session where the self-destruct email was being posted to the www.willselfdestruct.com website. One way to do this is to pick a couple of keywords from the message (such as "teaching" and "running") and add them to the Keywords tab of NetworkMiner. You will then have to press the "Reload Case Files" button in order to let NetworkMiner re-parse the nitroba.pcap file while looking for these keywords. Look in the Context column for text that seems to be from the self-destruct message.
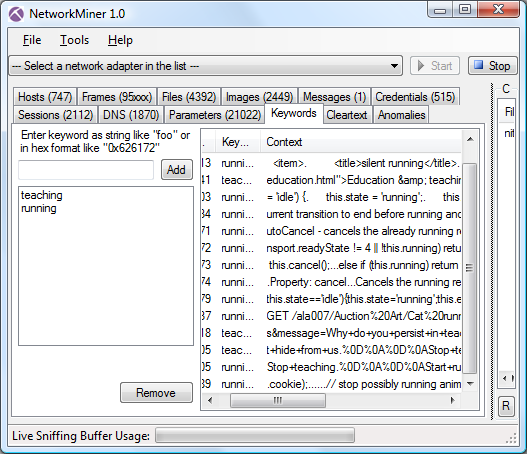
You can also take some time to browse through the other tabs of NetworkMiner... Who knows, maybe the self-destruct message is even easier to find than you might expect? ;)
After you've identified the IP address of the machine from where the self-destruct message was sent you'll need to start looking for clues as to who is using the computer with that IP address. Here are a few suggestions for things to consider:
- At what point in time was the self-destruct message sent?
- Has the sender's IP address been used by one or several computers?
- What online services (webmail / social media / instant messaging etc.) has the user of this IP address been logged into?
Feedback to DEEP
I really enjoyed the Nitroba case, and thought it was a really good training case to be used for educational purposes. Thanks Naval Postgraduate School's Digital Evaluation and Exploitation (DEEP) group for creating this network forensics case!
Posted by Erik Hjelmvik on Thursday, 16 June 2011 18:31:00 (UTC/GMT)
Tags: #Netresec


